Penetration Testing as a Service (PTaaS) and continuous vulnerability scanning have become standard components of modern security programmes.
DevOps teams in SaaS and fintech organisations move fast, releasing code continuously, updating infrastructure frequently, and relying on automated delivery pipelines. To keep pace, many are turning
Today, software is built and delivered faster than ever, but that speed has come with a cost. The integrity of the software supply chain is now one of the most actively targeted areas in cyber security.
CVE-2025-55182 is a newly disclosed critical vulnerability (CVSS 10.0) affecting React Server Components (RSC), enabling attackers to execute arbitrary code on
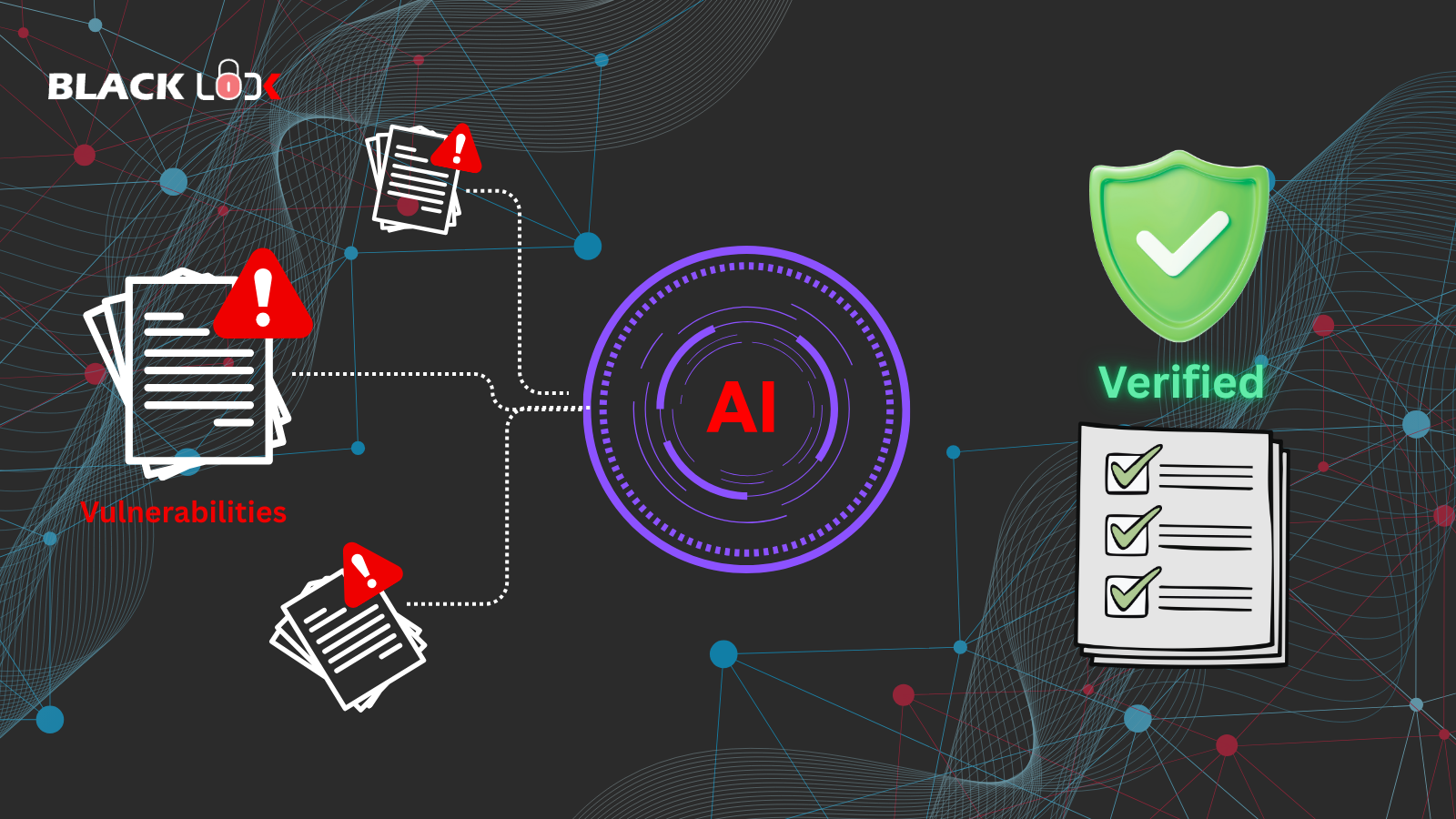
Automated vulnerability revalidation with AI agents is changing how organisations maintain security assurance.
Cybersecurity has become a baseline expectation for doing business, and New Zealand businesses are part of that global reality. The Government Communications Security Bureau (GCSB)
Artificial intelligence initiatives, and particularly large language models (LLMs), are moving from research labs into production systems at unprecedented speed.
Often called the CKC or “the cyberattack lifecycle”, the Cyber Kill Chain is a strategic security model that chains the security vulnerabilities together to form a real-world exploit.
We are proud to announce that Blacklock Security has achieved CREST accreditation for our penetration testing services.
.png)





.png)
.png)
